Comprehensive and In-Depth Detection
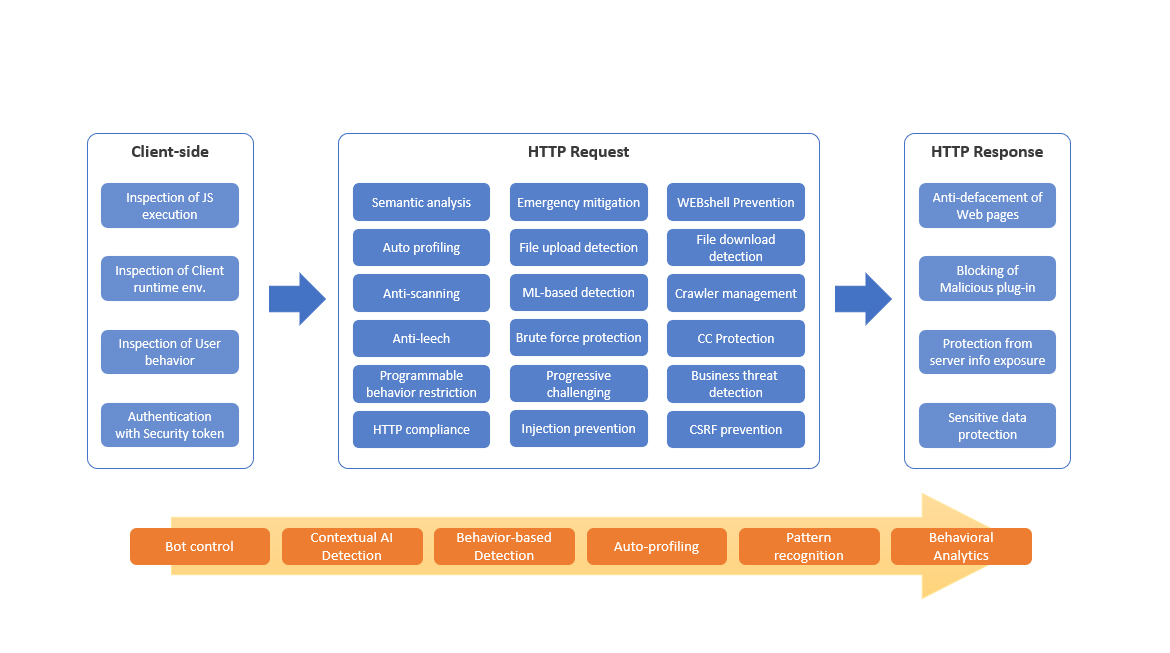
MaxiSafe conducts full-path detection, covering all stages from client-side initialisation to HTTP request processing and HTTP response delivery. This multi-phase inspection ensures accurate identification of abnormal behaviour, bots, and threats across the entire interaction chain.
Detection is performed in three stages:
-
Client-Side Detection:
Captures real-time behaviour and environment signals before a request is issued. -
HTTP Request Detection:
Inspects and classifies incoming traffic based on headers, payloads, and behavioural indicators. -
HTTP Response Detection:
Identifies data leakage, scraping patterns, and abnormal response access.
MaxiSafe integrates detection results with risk-based scoring and enforces adaptive policies at the edge through bot control, contextual detection, and fingerprint profiling.
Client-Side Detection
Client-side detection enhances accuracy and context awareness before request processing. The detection is done via lightweight interrogation executed in the client environment and fingerprinting mechanisms that gather execution signals.
-
Environment Fingerprint Collection
Collects device/browser characteristics, including canvas, font, audio, and WebGL fingerprints. -
Browser Identification
Validates browser integrity and detects headless or emulated environments to prevent spoofing. -
JavaScript Execution Verification
Confirms client-side script execution and interaction capability. -
Platform Authentication Check
Evaluates OS, browser, and hardware authentication against expected combinations. -
Challenge Response Handling
Issues challenge pages to evaluate automation resistance.
Detection result:
- Risk level is determined (normal, suspicious, high-risk).
- Requests from non-compliant clients are redirected, challenged, or blocked.
- Fingerprint IDs and risk scores are logged for downstream correlation.
HTTP Request Detection
MaxiSafe inspects each inbound HTTP request at the edge before forwarding it to the origin server. This stage includes protocol compliance checks, behavioural analysis, and policy-based filtering:
-
Bot Control
Detects and mitigates traffic from malicious or non-compliant bots using signature matching, fingerprint behaviour, and challenge-based validation. -
Contextual Detection
Analyses request context including navigation flow, referer chain, user interaction history, and time anomalies to identify suspicious behaviour patterns. -
Custom Rules Detection
Enforces user-defined rules based on HTTP headers, parameters, paths, cookies, or query values. Supports logic conditions and regex matching. -
Header Inspection
Identifies malformed, spoofed, or missing headers such as User-Agent, Referer, Host, and Accept-Language to detect automation or evasion tactics. -
Rate Limiting and Frequency Analysis
Flags abnormal request frequency from a given client or IP range. Supports path-specific and burst-based thresholds.
Advanced Detections
- HTTP Method Validation
- IP Reputation Check
- Request Payload Anomaly Detection
- Parameter Tampering Detection
- Protocol Abuse Detection
HTTP Response Detection
Response-stage detection ensures sensitive content is not unintentionally exposed and helps detect scraping or automated content mining, including:
-
Data Leakage Detection
Scans response payload for exposed tokens, keys, or configuration values. -
Content Scraping Pattern Detection
Detects repeated or automated access to structured content, such as product pages or price listings. -
Behavioural Loop Detection
Identifies repetitive access patterns consistent with scraping or brute-force cycles.