Bot Management
MaxiSafe’s Bot Management provides a multi-layered defense mechanism that integrates validation, token-based verification, behaviour-based analysis, and progressive challenges to accurately detect and mitigate malicious bot activity in real-time. By leveraging comprehensive client profiling and adaptive challenge mechanisms, MaxiSafe ensures effective threat mitigation while maintaining a seamless user experience.
Intelligent & Proactive Bot Control
A Layered Bot Control
MaxiSafe employs a layered bot control system that combines static validation, token-based verification, behavioural analysis, and challenge-response mechanisms. This approach ensures accurate detection and interception of malicious bots while preserving legitimate access:
- Static-Based Control
Detects known malicious bots through passive inspection of request headers, user-agent strings, and device fingerprints. Static analysis helps block bots that rely on spoofed or anomalous identifiers. This method is effective against bots using predictable patterns or blacklisted signatures. - Token-Based Control
Validates session authenticity using secure tokens that legitimate clients can acquire and present correctly. This technique ensures that only verified clients can maintain or initiate a session, preventing token replay and session hijacking by automated bots. - Behaviour-Based Control
Analyses user interaction patterns inreal-timee, such as navigation flow, mouse movement, and input timing, to distinguish human users and legitimate bots from automated malicious activity. Behavioural profiling allows for adaptive response to emerging threats. - Challenge-Based Control
Applies progressive validation techniques, such as JavaScript execution, cookie checks, and CAPTCHA, to confirm human presence. These challenges are selectively triggered for suspicious or unverified clients, adding an extra layer of verification without affecting normal users.
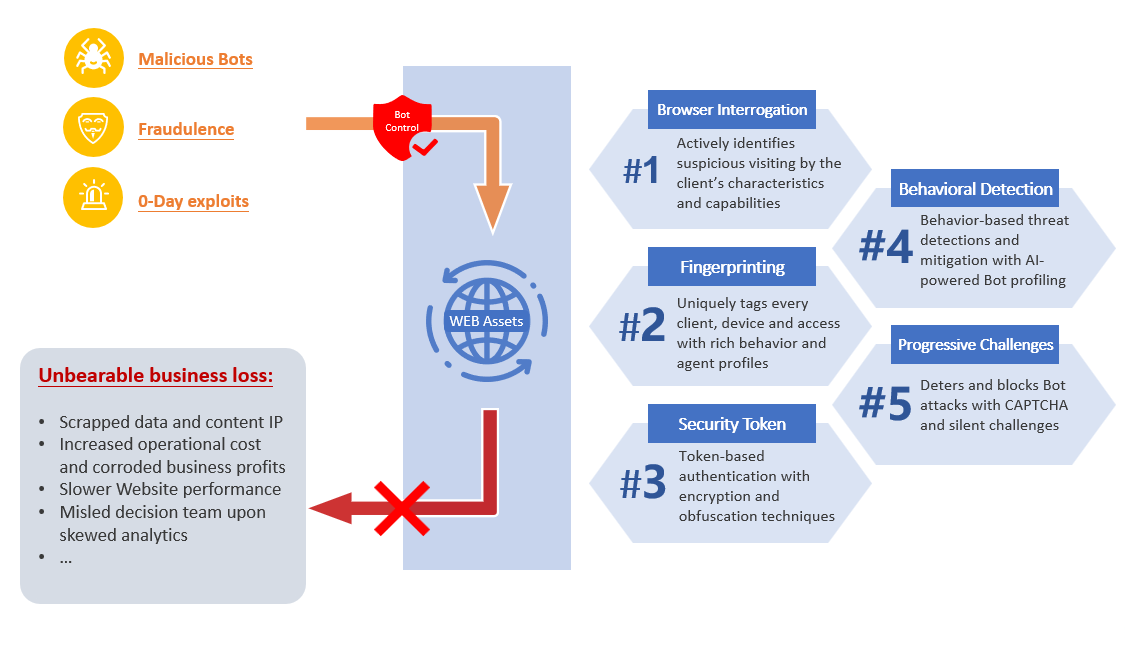
Key Components
MaxiSafe combines client-side interrogation, unique identity tracking, token validation, behavioural analytics, and adaptive challenges to ensure proactive and intelligent bot control. These five core mechanisms work together to deliver high detection accuracy with minimal user disruption:
-
Browser Interrogation
- Conducts in-depth analysis of client characteristics and capabilities to identify suspicious activity.
- Detects indicators of automated tools, headless browsers, and browser anomalies that deviate from typical user behaviour.
-
Fingerprinting
- Assigns unique identifiers to each client, device, and session based on behaviour patterns and agent profiles.
- Tracks user interactions, navigation paths, and request frequencies to identify malicious automation and repeated attack attempts.
-
Security Token
- Implements token-based authentication with encryption and obfuscation techniques to validate client requests.
- Prevents session hijacking and unauthorized access by correlating session data with predefined behavioural baselines.
-
Behavioural Detection
- Utilizes AI-powered profiling to detect deviations from typical interaction patterns.
- Identifies suspicious activities such as rapid requests, credential stuffing, and scraping attempts based on behavioural analysis.
-
Progressive Challenges:
- Deploys dynamic challenges based on assessed risk levels, starting with silent checks and escalating to CAPTCHAs for higher-risk interactions.
- Adjusts challenge intensity based on anomaly severity to maintain user experience while effectively deterring automated threats.
Comprehensive Threat Coverage
MaxiSafe’s Bot Management effectively addresses multiple bot-driven threats, including:
- Malicious Bots: Detects and blocks automated attacks aimed at data scraping, credential stuffing, and denial of service.
- Fraudulence: Identifies fraudulent access attempts based on behavioural inconsistencies and suspicious navigation paths.
- 0-Day Exploits: Mitigates emerging threats by analysing anomalous requests and obfuscated payloads without relying solely on predefined rules.
Token-Based Bot Control
Token-based bot control in MaxiSafe leverages Security Tokens to validate client requests through encryption and obfuscation techniques, ensuring secure session management and preventing unauthorized access. The verification process is structured as follows:
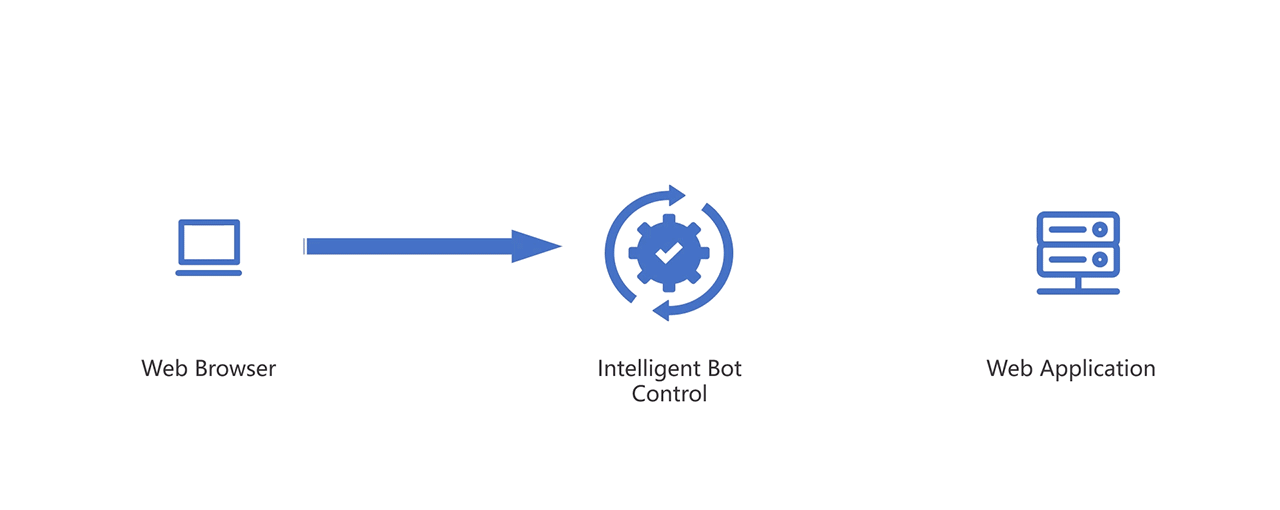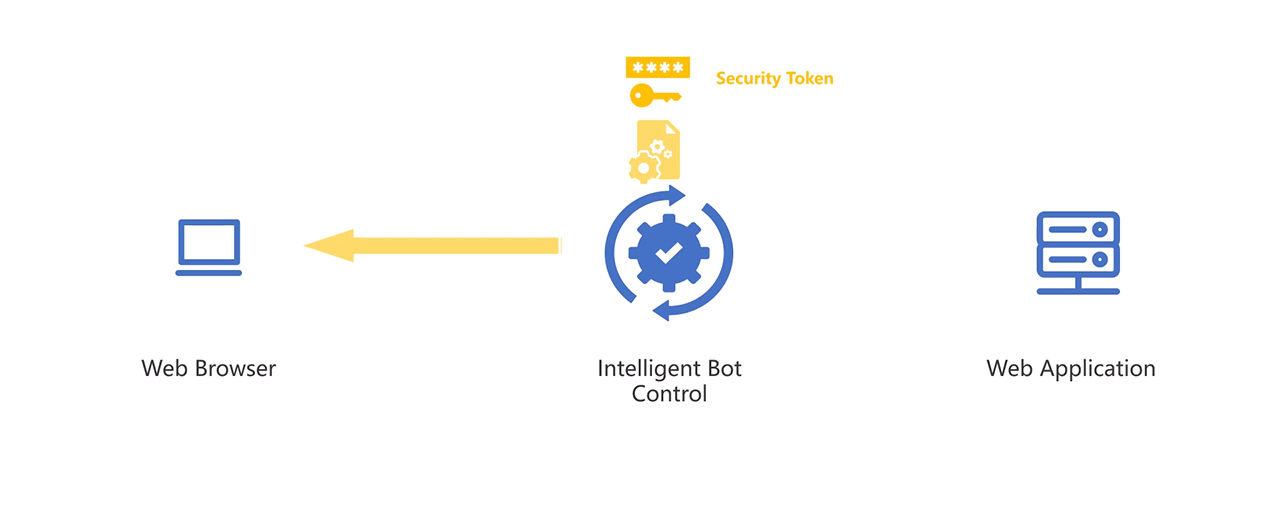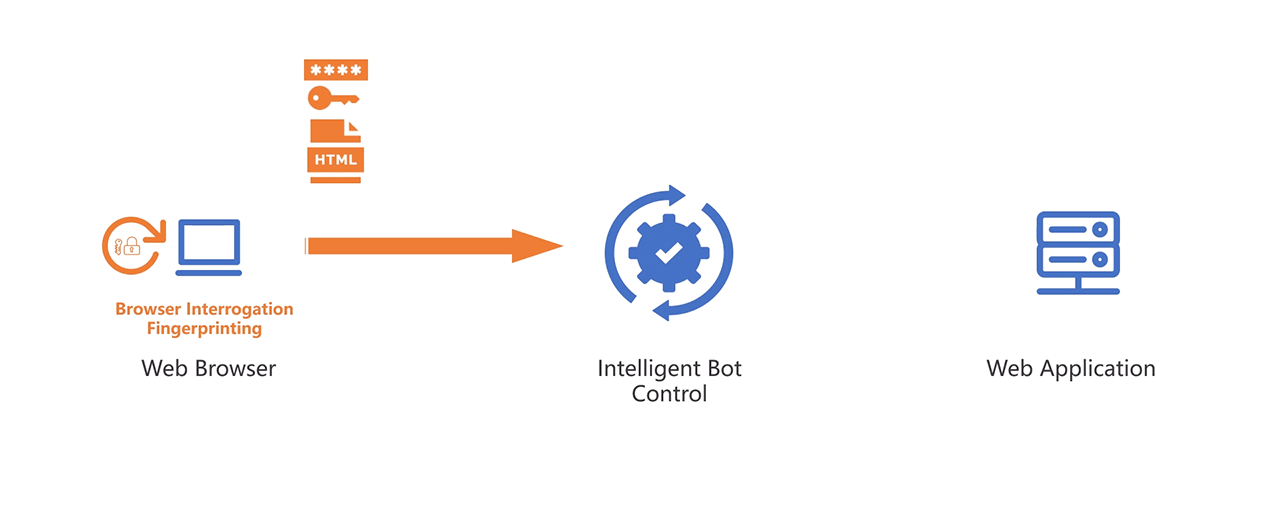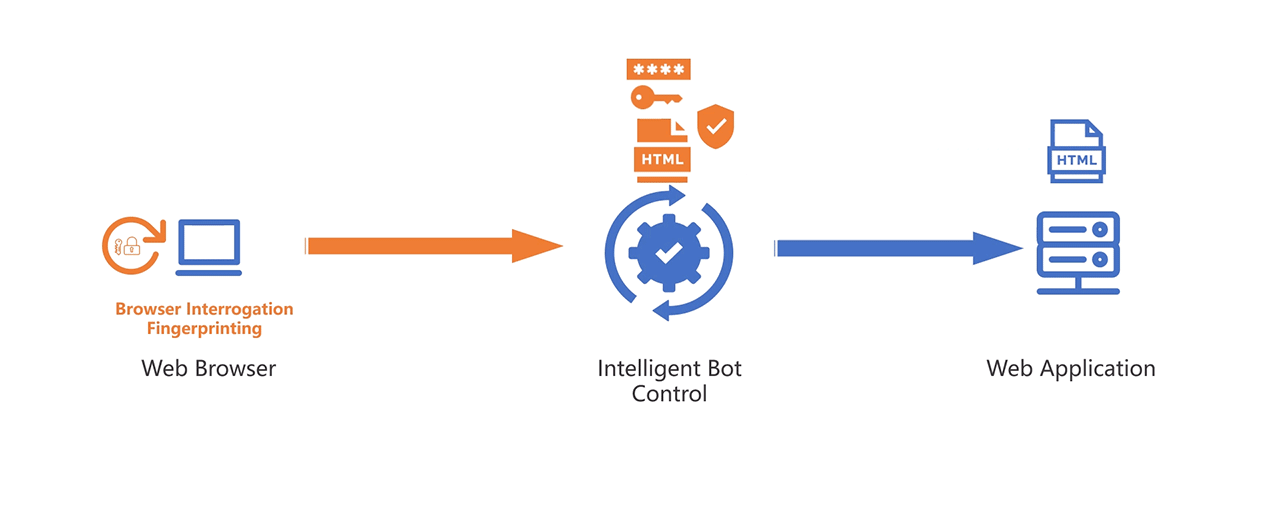
-
Token Issuance and Assignment
- When a request is initiated, the Intelligent Bot Control module issues a security token to the client.
- The token is encrypted and embedded with session data, including client fingerprinting and behavioural metrics.
-
Token Validation and Analysis
- Upon subsequent requests, the system validates the token, verifying its authenticity and matching it against the previously recorded session data.
- The validation process includes decryption and inspection of the token content to detect anomalies in session parameters.
-
Advanced Interrogation and Behavioural Analysis
- If the token data deviates from the expected session profile, the system initiates Browser Interrogation and Fingerprinting to conduct deeper analysis.
- Behavioural patterns are cross-referenced with baseline profiles to assess potential threats, such as automation tools or rapid request sequences.
-
Escalation and Progressive Challenges
- For requests flagged as suspicious, the system initiates progressive challenges based on threat severity.
- The escalation path includes:
- Silent checks for low-risk requests, leveraging client fingerprinting and browser interrogation.
- CAPTCHA or interaction challenges for high-risk requests, requiring additional verification to proceed.
-
Mitigation and Response
- Verified requests proceed to the Web Application, maintaining seamless access for legitimate users.
- Requests that fail verification are blocked, preventing further access and mitigating potential bot-driven attacks.
Advantages of Bot Management
-
Zero Customer Disruption
- Maintains a seamless user experience through invisible protections that do not impact legitimate users.
- Implements sophisticated detection techniques that are difficult for attackers to bypass.
-
Real-Time Defense
- Autonomous threat response powered by AI and machine learning, allowing immediate mitigation of emerging threats.
- Continuous monitoring ensures threats are detected and neutralized before they impact business operations.
-
Ease and Transparency
- Automated updates and minimal configuration reduce the operational burden on IT and security teams.
- Comprehensive monitoring provides visibility into attack patterns and bot interactions.
-
Unbeatable Accuracy
- Ultra-low false positive rate (0.001%) ensures precision targeting of malicious bots without affecting legitimate traffic.