MaxiSafe Solutioning Triad
MaxiSafe integrates client analysis, a comprehensive security posture, and intelligent threat control to protect web assets while ensuring performance and compliance, delivering secure, accelerated, and resilient web services.
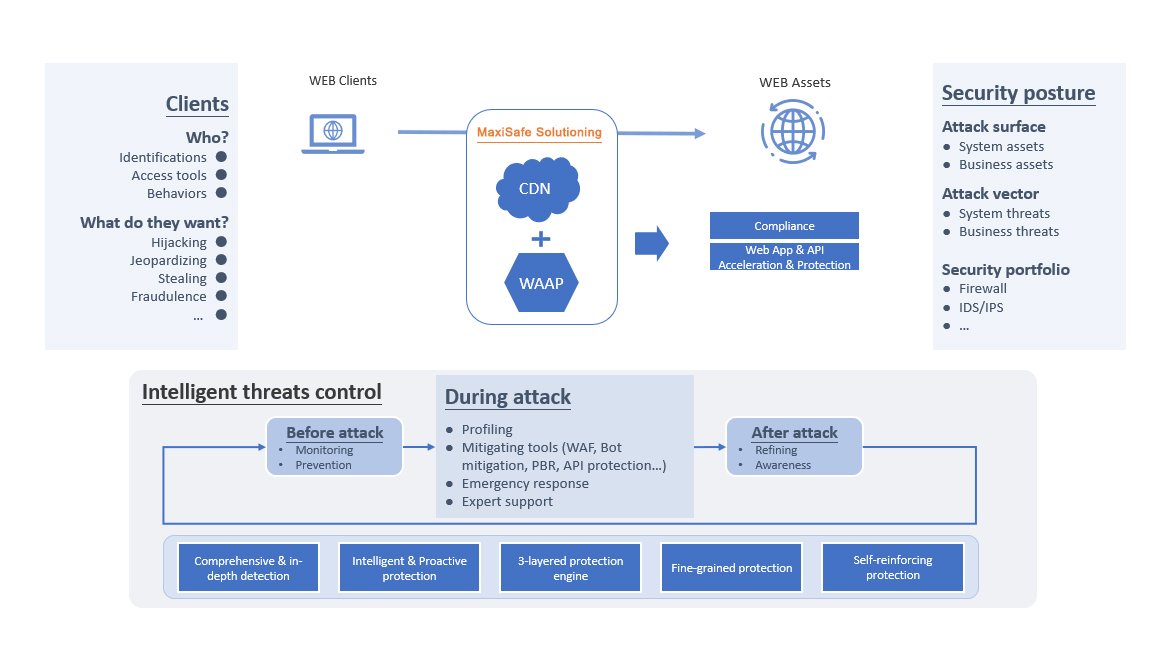
Clients
MaxiSafe processes all inbound client traffic, from browsers and apps to automated tools, by examining identities, access patterns, and behavioural attributes. This enables proactive threat filtering before the requests reach the origin.
- Who is accessing?
- Identifications: IP address, session tokens, fingerprints, etc.
- Access Tools: Browsers, scripts, verified/malicious bots, etc.
- Behaviours: Request frequency, navigation path, anomalies, Human Interface Device (HID) operations, etc.
- What are their intentions?
- Hijacking sessions and tokens.
- Jeopardising application uptime or integrity.
- Stealing data or content.
- Committing fraud, such as fake logins or automated abuse.
All traffic is routed through MaxiSafe, which applies content acceleration and WAAP-based security enforcement.
Security Posture
MaxiSafe defines a comprehensive and layered defense strategy targeting system-level and business-level threats, covering attack surface, attack vector and security portfolio.
- Attack Surface:
- System Assets: Web servers, APIs, storage endpoints, etc.
- Business Assets: Transaction data, user inputs, business logic, etc.
- Attack Vectors:
- System Threats: DDoS, port scanning, protocol abuse, etc.
- Business Threats: Credential stuffing, logic abuse, scraping, etc.
- Security Portfolio:
- AI-WAF with customisable rules.
- Bot management and browser fingerprinting.
- API protection with rate limiting and access policies.
- IDS/IPS: signature-based intrusion detection and prevention.
- Logging and compliance modules for policy audits and traceability.
- Extended with modules for threat intelligence integration, anomaly detection, and advanced access control.
Intelligent Threats Control
MaxiSafe executes lifecycle-based threat handling across three operational stages: before attack, during attack, and after attack.
- Before Attack:
- Monitoring: Real-time traffic analysis and anomaly detection.
- Prevention: Predefined and AI-trained rules for early filtering.
- During Attack:
- Profiling: behavioural fingerprinting to detect and classify threats.
- Mitigation Tools:
- WAF for application-layer protection.
- Bot mitigation for automated traffic.
- API protection and policy-based routing.
- Emergency Response: Live threat response and incident handling.
- Expert Support: Send email to support@conversant.tv to get expert support.
- After Attack:
- Refinement: Updating policies and detection models by using behavioural analysis.
- Awareness: Post-event analysis and security insight delivery.
MaxiSafe handles client profiling, security posture, and lifecycle threat control through a unified detection and enforcement engine. Its architecture enables deep traffic analysis, behavioural correlation, and real-time mitigation across all layers. The following capabilities form the core of this multi-layered defense model.